Teachers’ Resources, Module 1:
Your information footprint is larger than you think
About This Lesson Module:
The lesson elements in this module teach students about the privacy principle “Your information is larger than you think”. They are designed to be independent and flexible, so you can incorporate them into any size lesson plan.
Summary of Learning Objectives: Students can enumerate ways their online and offline activities contribute to their information “footprint”; students can use privacy settings and critical thinking skills to limit the exposure of their footprint.
Target Age: High school, college undergraduate.
Learning Objectives
- Students can give examples of ways their online and offline activities generate digital footprints, within each of the following broad categories: intentional posting/online activities, metadata attached to posts, information transmitted by devices, and others collecting or posting information about them.
- For at least one example of an activity that generates digital footprints, students can explain (at least in non-technical terms) how that activity generates those footprints.
- Students can enumerate some factors that affect how many people or entities can see the data in their information footprint, including (minimally) privacy settings and third-party data sharing, and give examples of potential negative consequences of exposure.
- Students can explain how the amount of information available about them, and how many people have access to it, is affected by mining of data from different sources to form a picture of each person, and can give examples of inferences that can be drawn by data-mining.
- Students can give examples of available privacy settings for apps, online services, and devices they use frequently, and explain why they would choose particular settings based on their information-sharing preferences.
- Students can suggest some potential uses apps and online services might have for particular types of personal data they typically request access to, and evaluate whether those uses would likely be beneficial, neutral, or harmful to the student.
Curriculum Standards Addressed
Lesson elements in this module can be used to address the following computer-science curricular standards.
AP Computer Science Principles Curriculum Framework
Elements substantially address the following Essential Knowledge under Big Idea 3, Data and Information:
- EK 3.3.1F. Security and privacy concerns arise with data containing personal information.
Elements substantially address the following Essential Knowledge under Big Idea 7, Global Impact:
- 7.3.1G. Privacy and security concerns arise in the development and use of computational systems and artifacts.
- 7.3.1H. Aggregation of information, such as geolocation, cookies, and browsing history, raises privacy and security concerns.
- 7.3.1J. Technology enables the collection, use, and exploitation of information about, by, and for individuals, groups, and institutions.
The following Essential Knowledge is also touched on:
- Under Big Idea 3: Data and Information: 3.2.1G, 3.2.1H.
- Under Big Idea 6: The Internet: 6.1.1A, 6.1.1C, 6.1.1E.
- Under Big Idea 7: Global Impact: 7.1.1I, 7.1.1J, 7.1.1K; 7.1.2G. 7.3.1D, 7.3.1K, 7.3.1L, 7.3.1M.
CSTA K–12 Computer Science Standards (Level 3 — High School)
Elements substantially address the following learning objective under Level 3, Course 3A: Computer Science in the Modern World:
- CI.10. Describe security and privacy issues that relate to computer networks.
The following learning objectives are also touched on:
- Under Level 3, Course 3A: Computer Science in the Modern World: CD.1; CI.4.
- Under Level 3, Course 3B: Computer Science Concepts and Practices: CI.2.
ACM Computer Science Curricula 2013 (CS2013) Guidelines (Undergraduate)
The following Learning Outcomes are touched on:
- Under Information Assurance and Security: Threats and Attacks 5; Security Policy and Governance 1, 2.
- Under Social Issues and Professional Practice: Social Context 9; Privacy and Civil Liberties 3.
“Engage” Activities:
Use one or more of these lesson elements to introduce the topic and ignite students’ interest.
Quick Opening Questions (Whole-Class Mini-Discussion)
Estimated Time: 2-5 minutes.
What You’ll Need: Blackboard/whiteboard (optional).
Ignite Question
Have you ever been surprised at how a website knew certain things about you?
Fanning the Fires:
- Do you see ads related to what you’re interested in?
- Are the ads that you see different than the ads your friends see?
- Do websites sometimes know your location even when you don’t tell them?
Quick Knowledge Check
What is an information footprint?
Note: The terms “information footprint” and “digital footprint” are generally used interchangeably. Either term can refer either to the individual “footprints” or bits of information someone leaves behind as they go through life, or to the overall “footprint” made up of all of the information there is about someone online. In the TROPE materials, we usually(!) use “information footprint” to refer to the overall sum of information about someone, but both definitions are valid.
News Stories You Can Use
The Quick Hook
Estimated Time: 2-3 minutes per story.
What You’ll Need: Computer and projector (optional).
These news items can be used to illustrate the real-life consequences of privacy breaches. If you have a computer and projector, you can show the stories on a screen as you talk about them. If not, you can simply summarize them verbally.
Burger King Employee Stands on Lettuce: Busted by Internet
- Summary: A Burger King employee posts a picture of himself standing in the ingredients; other 4Chan users use the GPS metadata attached to the picture to figure out which franchise it is; employee gets fired.
Betrayed by Metadata: John McAfee Admits He’s Really in Guatemala
- Summary: The antivirus-company founder is accused of murder in Belize; escapes to Guatemala with a reporter who posts a geotagged photo; after much confusion, admits the GPS was correct; gets arrested.
- Content Advisory: This NPR article is itself appropriate for all ages, but it contains a link to a Vice Magazine article with taboo language, which is, well, on a website called Vice…
The Strange, Sad Saga of Russia’s ‘Sergeant Selfie’
- Summary: Russia claims there are no Russian soldiers in a particular area of the Ukraine; a Russian soldier posts a selfie that shows up on the Instagram map as having been taken in that area; media brouhaha ensues and soldier is (as far as anyone can tell) discharged.
Note: Given the imprecision of Instagram mapping, it is not clear whether the soldier actually was in the Ukraine. But, in combination with some translation confusion around another post, the photos sure did cause some trouble, especially since a passenger airliner was shot down in that area around that time. This can also be a lesson in media hype obscuring subtleties, especially when reporters don’t know how geotagging works.
Optional Extension
Estimated Additional Time: 5-7 minutes per story.
For each news item, ask the students:
- What kind of digital footprints did this person leave?
- Did they know they were leaving footprints?
- How did other people find them?
- What were the consequences?
- How could the situation have been avoided?
Other Media Resources for "Engage": The Amazing Mind Reader
Estimated Time: 4-6 minutes.
What You’ll Need: Computer, projector, and speakers.
Summary: This video shows a “mind reader” who seems to be able to see the details of people’s private lives, from their friends’ names to their bank account numbers — but when the curtain drops, we see that all the information was available online.
Video: Amazing Mind Reader Reveals His ‘Gift’
When to Use – Options:
- If you’re using the mind-reader video to open the lesson: Let the students try to guess what his secret is.
- If you’re introducing this video after the opening discussion: Before playing the video, ask the students how much they think someone could find out about them from their digital footprints.
- Content Advisory: Among the details revealed are that someone spends a lot on alcohol and that someone has multiple love interests (the tone implies sex partners).
Produced by Febelfin, the Belgian Financial Sector Federation.
“Explore” Activities:
Use one or more of these lesson elements to ground students’ learning in firsthand experience with how privacy works.
Interactive App: Ready or Not?
Estimated Time: 5-8 minutes.
What You’ll Need: Computer and projector.
This app shows how people could use someone’s social-media posts to find them in the physical world. The user types in a Twitter or Instagram ID, and the app uses GPS data attached to their posts to create a timeline and heatmap of where they’ve been posting from recently.
Ready or Not? App: http://app.teachingprivacy.org
 Initial Screen (Home) |
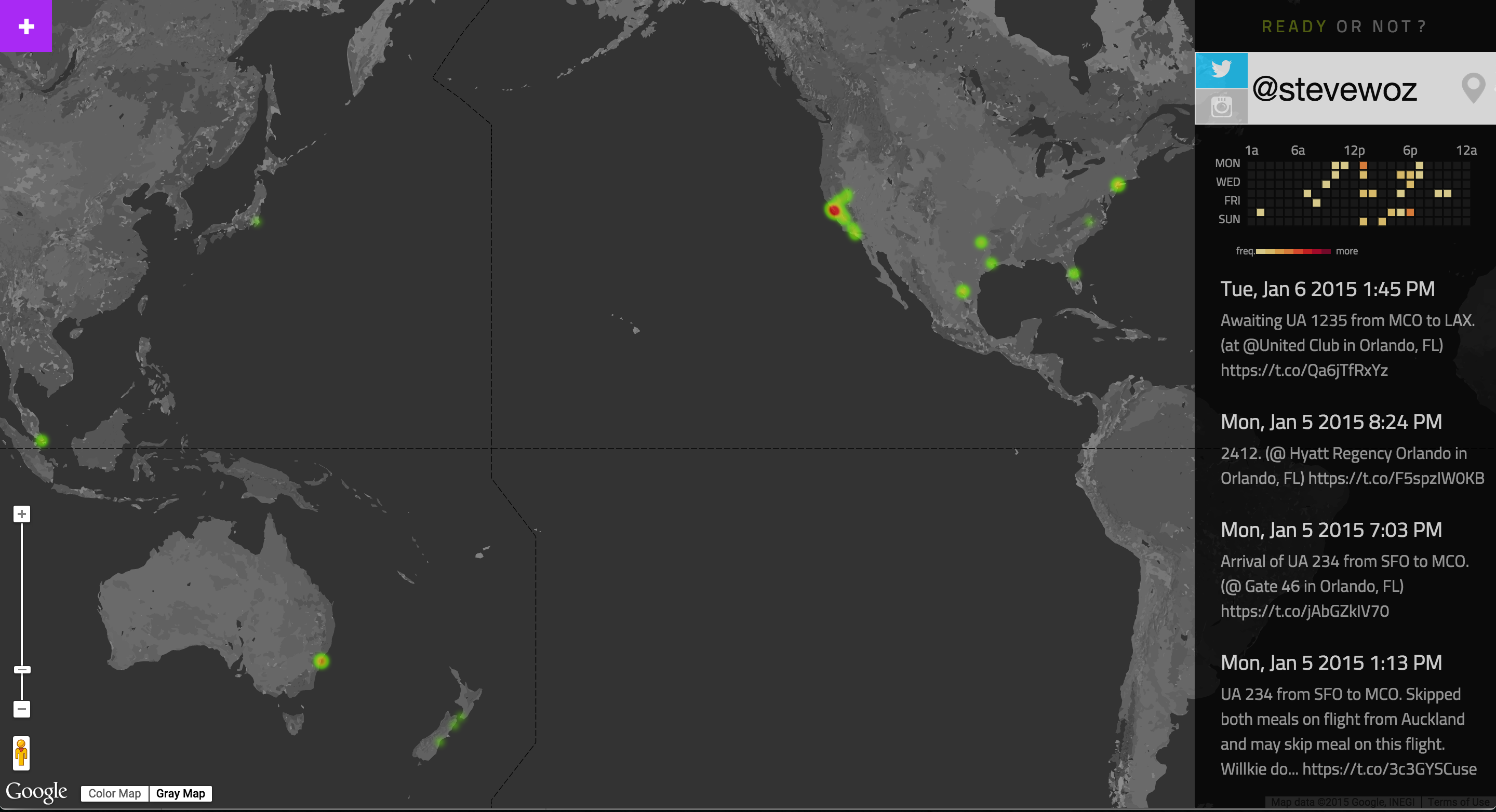 Heatmap Results for a Twitter ID |
Options:
- Use your own computer and project the app on a screen. Ask students to volunteer to have you type in their Twitter or Instagram IDs. (They don’t need to log in.)
- If you’re in a computer lab or students are allowed to use mobile devices in class, split them into pairs and have them try the app themselves.
Notes and FAQs:
- If a student has Location Services turned off on their phone or their Twitter/Instagram accounts, they won’t get any results, but the app will suggest names of semi-famous people who share locations.
- You can click on a time-slot in the created timeline to see markers for those posts on the map. Clicking on the markers then shows Streetview images from that location.
- You can hover over the “Ready or Not?” title to see instructions for how to use the app.
 Hover Over Title for Instructions |
 Click on a Time-Slot for Location Markers |
 Click on a Marker for Streetview Images |
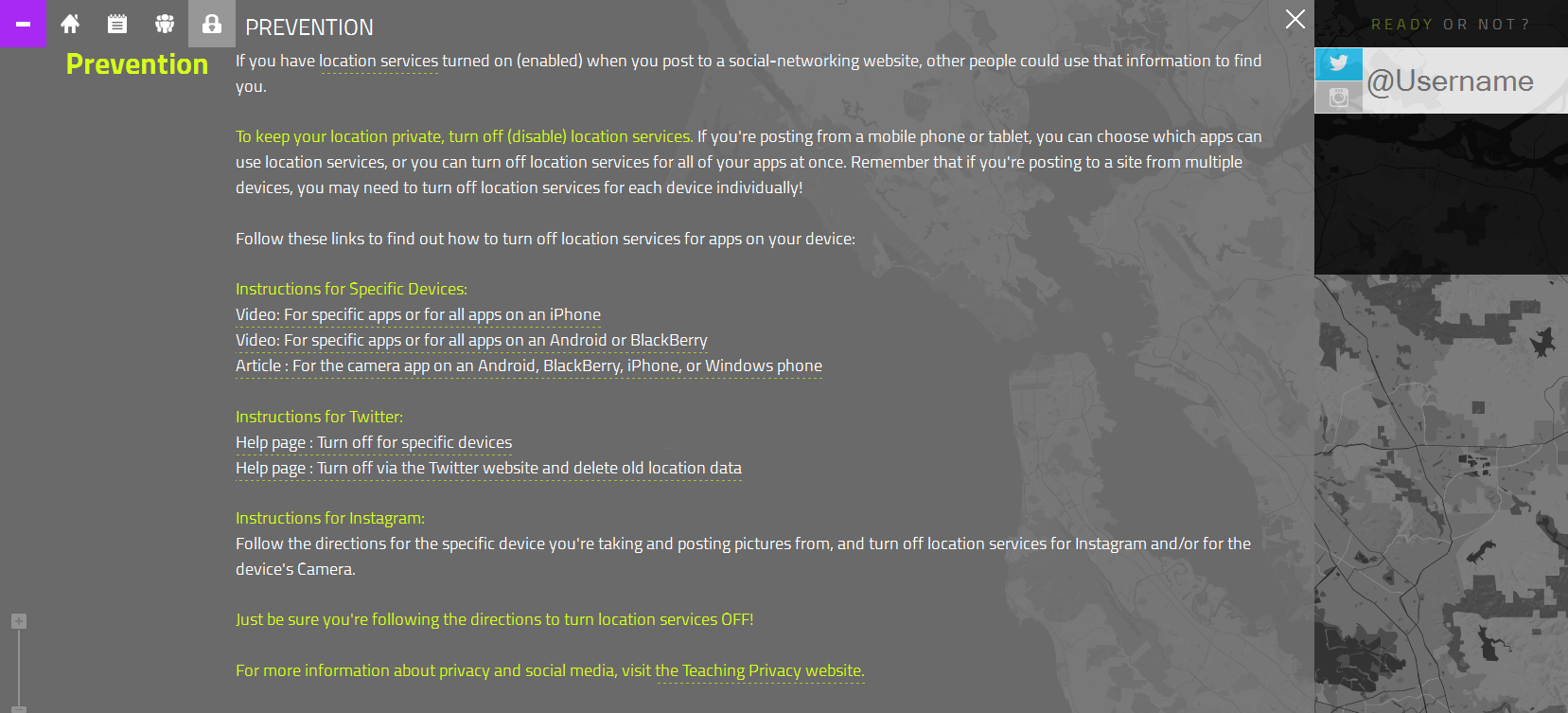 Click on Lock Symbol for “Prevention” Screen |
The How-To — Minimizing Your Information Footprint:
- If you’re not using one of the fuller privacy-skills activities among the “Elaborate” elements, this is a good time for a quick how-to.
- The app includes a “Prevention” page that explains how to turn off Location Services on your phone and on the Twitter website/app. Go to the + in the upper left to get the menu, then click on the lock symbol (“Prevent”).
This information is also on the Teaching Privacy “Step Up Your Settings” page.
Whole-Class Brainstorm & Discussion: What Kind of Data Do You Generate?
Estimated Time: 10-15 minutes.
What You’ll Need: Blackboard/whiteboard (optional).
Ask students to give examples of different things they do in a day (online or offline). Examples can be written on the board. Pick a few interesting examples and ask:
- What kind of data does that activity generate?
- What could other people do with that information? What could they figure out about you?
- Is that something you want them to know about you?
Some examples you can start them off with:
- What data is generated by a Facebook post?
- Generates: The text in the post/pixels in the picture, time and date posted, IP address (unique identifier) of the device you posted from, what browser or app you used, geo-coordinates (if you have Location Sharing on), how many edits you made and what you changed, who’s tagged in the photo… More information is added over time: Who viewed the post, how long they were on the page, who liked or commented (and the time, IP address, etc. for that), where they went next… (Some of this information is viewable by other users and some is Facebook-internal only, like IP address, editing history, and viewing data.)
- Can Be Used For: Text analysis/image recognition could be used to target ads to your interests; comments and likes could be used to figure out who you really interact with (out of all your Friends); with Location Sharing (or your IP address, depending on the device type and whether they have the skills), someone can figure out where you are right now/where you usually are this time of day…
- What data is generated when you just look at a web page, without clicking on anything?
- Generates: Your IP address, the browser and app you used, how long you looked at the page… ISPs and LAN administrators can also capture this data. Depending on the site and your setup, it may also generate: A record in the cookie file on your computer, some kind of browser fingerprint, a record of where your mouse moved and paused…
- Can Be Used For: All of the above could be used to compile a record of what you’re interested in, to target advertising (to you specifically and to your demographic group), to monitor your browsing habits…
- What data is generated by riding the bus or subway?
- Generates: If you have a pass you paid for with a credit card, it records when and where you got on and off; if the vehicles have security cameras, they record your image.
- Can Be Used For: To locate you now, or figure out your daily habits; camera footage can be used to identify you (with facial-recognition software) and see what you did…
Extended Version:
Ask students to name some of the apps, sites, and devices they use. What kind of data do those apps/sites/devices collect about you?
“Explain” Activities:
Use one or more of these lesson elements to provide students with important facts and underlying concepts.
Video for "You're Leaving Footprints"
Estimated Time: 5 minutes.
What You’ll Need: Computer, speakers, and projector.
“You’re Leaving Footprints” explores the many factors and activities that add to each person’s information footprint, and describes some of the strategies we can use to limit our exposure. Part of the TROPE video series, with humorous illustrations by Ketrina Yim that turn each point into a memorable story.
Includes human-generated closed captions.
Slide Deck for "You're Leaving Footprints"
Estimated Time: 12-15 minutes.
What You’ll Need: Computer, projector, and speakers; copies of graphic organizer (optional).
These slides can be used for an overview lecture on the basic concepts underlying the principle “Your information footprint is larger than you think”. The slides are accompanied by Notes with details and examples to guide your lecture.
Access Slide Deck: “You’re Leaving Footprints”
Use the custom Graphic Organizer to help students follow along and take notes.
Access Worksheet: Graphic Organizer for “You’re Leaving Footprints” Presentation
Related Readings from Blown to Bits
The Blown to Bits textbook covers a wide spectrum of ideas related to Internet privacy, with a particular focus on the new, unique, ever-changing nature of the Internet.
Online Version: Blown to Bits: Your Life, Liberty, and Happiness After the Digital Explosion, by Hal Abelson, Ken Ledeen, and Harry Lewis
You can assign students all or parts of the following chapters for an in-depth but engaging exploration of the ideas covered in Module 5.
- Chapter 2: Naked in the Sunlight: Privacy Lost, Privacy Abandoned — Excerpt
- Chapter 3: Ghosts in the Machine: Secrets and Surprises of Electronic Documents — Excerpt
- Chapter 6: Balance Toppled: Who Owns the Bits? — Excerpt
- Content Advisory: Blown to Bits refers to STI outbreaks and discusses the dangers of sending sexually explicit content online.
“Elaborate” Activities:
Use one or more of these lesson elements to go deeper into the underlying concepts and/or let students practice important privacy skills.
In-Class Whole-Group Activity: Oh the Places You (and Your Data) Will Go!
Estimated Time: 40-50 minutes.
What You’ll Need: Computer and projector.
In this choose-your-own-adventure activity for the classroom, students make privacy decisions for a hypothetical person named Tatum and see what happens. In the process, they learn about the underlying privacy principles and are encouraged to actively engage with privacy issues.
How to Use:
- Speech bubbles in the lower-right corner of the slide indicate it’s time for class discussion.
- You can have the students decide as a class what Tatum should do at each choice point, or each student can keep track of their answers and compare outcomes at the end.
- Content Advisory: The Colbert Report excerpt near the end (sometimes) begins with an ad, which will have unpredictable content.
Other Notes:
- This activity is likely to take a full class period. It subsumes some of the other individual lesson elements in this module, including some of the Ignite and Brainstorming questions and two of the interactive apps, Ready or Not? and the EXIF Placer.
- There are four choice points in the story, but only three of the decisions affect the outcome at the end, as the first two choices both teach about location privacy.
- To prepare yourself for student questions, our backgrounders and references on information footprints and (lack of) privacy protections may be helpful.
Image Credits:
- Sunrise photo by Artur Maltsau, via Pixabay. Public domain.
- Crop of Steven Colbert from “Michelle Obama on The Colbert Report” by Lawrence Jackson for the White House, via Wikimedia Commons. Public domain.
- “Chat Bubbles” by Benjamin D. Esham, via Wikimedia Commons. License: Creative Commons Attribution-ShareAlike 3.0 Unported (CC BY-SA 3.0).
Programming Exercise: Mapping Geotagged Tweets
Estimated Time: 60-90 minutes.
What You’ll Need: Student computers that can access social media sites.
Programming Language: Python.
Prerequisite: Introductory Python lessons.
In this Python-based exercise, students use the Twitter API to extract the location data for a user’s tweets and a mapping library to create a heatmap of the locations. (A starter version of our “Ready or Not?” app used in the Explore exercise above.) Students are then asked to brainstorm about how extracting and comparing individual data points to form a combined picture can reveal additional, potentially sensitive information.
Download Programming Exercise (as Jupyter Notebook): Mapping Geotagged Tweets
Options:
- Pair Programming: We recommend you have students do this exercise in pairs or groups. At least one student in each pair/group will need to have or create a Twitter account. For tips on pair programming in the classroom, check out NCWIT’s pair programming kit.
- Depending on the dynamic of your classroom, it may be better to assign the optional extension (where students extract locations from their own tweets) as an individual exercise/homework rather than including it in the pair/small-group part (where their data could be exposed to each other).
- Brainstorming questions can be used for small-group or whole-class discussion or for individual writing.
Programming Concepts Taught:
- Use APIs and programming languages together to extract and analyze data.
- Use for loops to iterate actions over a dataset.
- Handle complex data objects using dictionaries and JSON format.
- Use multiple Python libraries in combination to create visualizations.
Caveat: An optional extension asks students to extract data from their own Twitter accounts if they have them, or the accounts of celebrities. However, we specifically do not recommend suggesting that they extract data from each other’s accounts as part of the exercise. This has the potential to result in embarrassing revelations that may actually be harmful, not just funny.
Of course, they may think of spying on each other without your help. If you think this is a concern, or that there may be issues within pairs/groups if you assign the extension, you may want to begin the activity by reemphasizing your rules for a safe classroom.
Teachers: Find out how to access the Mapping Geotagged Tweets exercise solutions.
Worksheet Activity: Managing Your Footprint
Estimated Time: 15-20 minutes for Option 1; 25-30 minutes for Option 2.
What You’ll Need: Copies of worksheet; computer and projector (optional).
In this activity, students fill out a worksheet where they decide who they really want to have see which information on the social-media sites they use most often. Then, either as homework (Option 1) or in class (Option 2), students check and update their privacy settings for those sites so the settings match what they said they want.
Download Worksheet: “Managing Your Footprint: A Privacy Settings Checklist”
Options:
- Have students fill out the worksheet grid in class, then they check and update their privacy settings as (non-gradeable) homework.
- If you’re teaching the class in a computer lab, or if all of the students have smartphones and they’re allowed to use them in class, the whole exercise can be done in class, including checking privacy settings.
Notes and FAQs:
- For some types of information (such as birthday), students may want the same level of exposure across all sites; you can suggest they draw an arrow across the row to show it’s all the same.
- Emphasize that students should think about how each type of information may lead indirectly to other types of information. For example, if they share their frequent locations (“Where I Post From”), they may be sharing their home address. If they share their birthday (as social information), they’re sharing their birthdate (legal/security-relevant information). (Not everybody thinks of that!)
- Encourage students to think about why they might want to have different standards for “Pictures of Me” vs. “Pictures of My Friends”. What are their friends’ privacy preferences?
- Students are directed to the Teaching Privacy “Step Up Your Settings” page for information about how to change various privacy settings. Of course, students may use apps/sites that aren’t listed there, or may use newer versions (depending on your timing). This can be an opportunity to ask students how they would go about finding privacy information for any given app.
- This exercise assumes students use social media. If there are students who don’t have any social-media accounts (even a school-network account), pick a couple of popular apps/sites and ask them what settings they would advise a friend to use.
“Evaluate” Activities:
Use one or more of these lesson elements to assess students’ understanding of the material and development of new skills.
Review Questions: Module 1 (Quiz/Homework)
Estimated Time: 10-12 minutes.
What You’ll Need: Copies of review sheet.
This learning assessment can be used as an in-class quiz or as homework.
Download Assessment: “You’re Leaving Footprints: Review Questions”
Teachers: Find out how to access the answer key for the Module 1 review questions.
More for Teachers
Resources and background information to help you brush up on the technical nitty-gritty and be prepared for student questions.
Coming soon! In the meantime, check out the main web page for You’re Leaving Footprints.
Other Recommended Classroom Resources for “You’re Leaving Footprints”
Activities and Videos: Social Networking; Revealing Too Much
- Target grades: K-12
- Summary: NetSmartz has activities and videos, including some that are very teen-friendly. Resources in the “Social Networking” and “Revealing Too Much” categories focus on the potential dangers and consequences of sharing personal information on a social-networking site.
- Produced by: The National Center for Missing & Exploited Children and Boys and Girls Clubs of America
- Link: http://www.netsmartz.org/Resources (Note: The link is to a page where you can retrieve activities by category and grade level.)